SIMULATION
A network administrator has been tasked with configuring a network for a new corporate office. The office
consists of two buildings, separated by 50 feet with no physical connectivity. The configuration must meet the following requirements:
Devices in both buildings should be able to access the Internet.
Security insists that all Internet traffic be inspected before entering the network. Desktops should not see traffic destined for other devices.
INSTRUCTIONS
Select the appropriate network device for each location. If applicable, click on the magnifying glass next to any device which may require configuration updates and make any necessary changes.
Not all devices will be used, but all locations should be filled.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
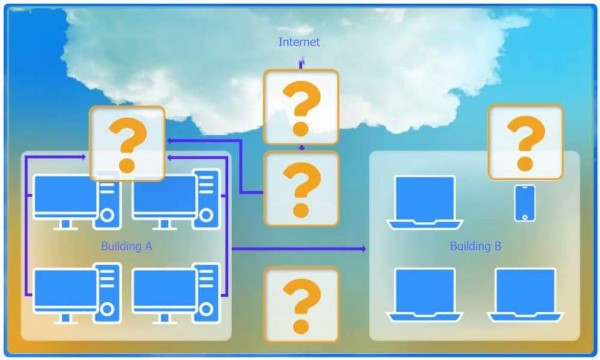

- See Explanation section for answer.
Answer(s): A
Explanation:
Central Device Connecting to the Internet (marked with a question mark at the top middle connecting to the Internet):
Device:
Firewall
Reason:
To inspect and filter all internet traffic before it enters the network, ensuring security compliance.
Device between Building A and the Internet (first question mark inside Building A): Device:
Router
Reason:
To route traffic between the internal networks (Building A, Building B) and the internet via the firewall.
Devices inside Building A (two question marks linked to desktops and server infrastructure):
Device:
Switch
Reason:
To connect all desktops and servers within Building A, ensuring that each device can communicate with others within the building without seeing traffic destined for other devices.
Device connecting Building A to Building B (question mark between the two buildings):
Device:
Wireless range extender
Reason:
Given the 50 feet separation and no physical connectivity, a wireless range extender can bridge this gap by extending the wireless signal from Building A to Building B, facilitating network access across both buildings.
Device inside Building B (question mark inside Building B):
Device: Switch
Reason: To provide connectivity for the devices in Building B, allowing them to connect to the network and access resources in Building A as well as the internet.