DRAG DROP (Drag and Drop is not supported)
You are a Power Platform developer.
Users report several access issues.
You need to resolve the user access issues.
What should you use? To answer, drag the appropriate security options to the correct scenarios. Each security option may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
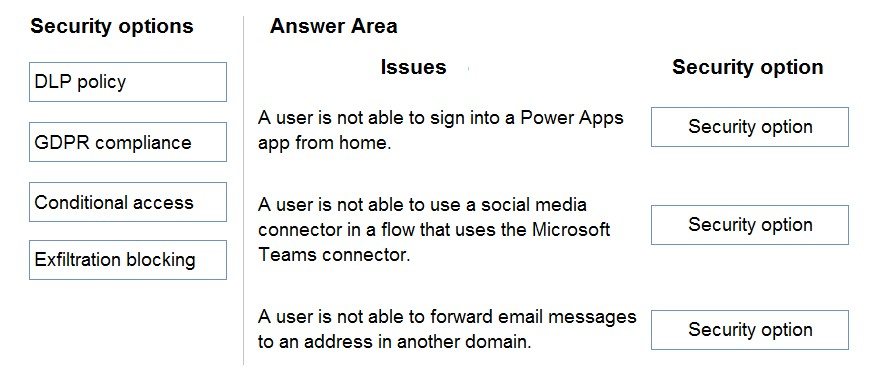
- See Explanation section for answer.
Answer(s): A
Explanation:

Box 1: Conditional access
You can limit access to users with block access by location to reduce unauthorized access. By using Conditional Access policies, you can apply the right access controls when needed to help keep your organization secure and stay out of your user's way when not needed. Conditional Access analyses signals such as user, device, and location to automate decisions and enforce organizational access policies for resources.
Box 2: DLP policy
DLP policies enforce rules for which connectors can be used together by classifying connectors as either Business or Non-Business. If you put a connector in the
Business group, it can only be used with other connectors from that group in any given app or flow. Sometimes you might want to block the usage of certain connectors altogether by classifying them as Blocked.
Box 3: Exfiltration blocking
Email exfiltration controls for connectors
Microsoft Exchange enables admins to disable email autoforwards and autoreplies to remote domains for external recipients. Exchange does this by using message-type headers, such as Auto Forward received from Outlook and Outlook on web clients.
Reference:
https://docs.microsoft.com/en-us/power-platform/admin/restrict-access-online-trusted-ip-rules https://docs.microsoft.com/en-us/power-platform/admin/wp-data-loss-prevention https://docs.microsoft.com/en-us/power-platform/admin/block-forwarded-email-from-power-automate