The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
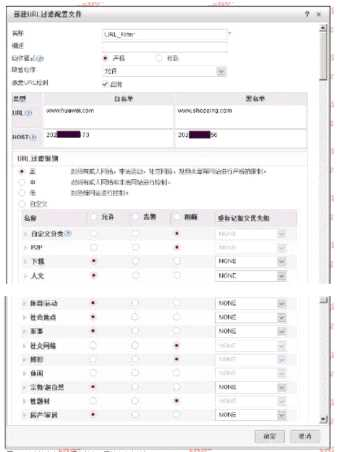
- The firewall will first check the blacklist entries and then the whitelist entries.
- Assuming that the user visits the www.exzample.com website, which belongs to the categories of humanities and social networks at the same time, the user cannot access the website.
- The user visits the website www.exzample.com, and when the black and white list is not hit, the next step is to query the predefined URL category entry.
- The default action means that all websites are allowed to visit. So the configuration is wrong here.