Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
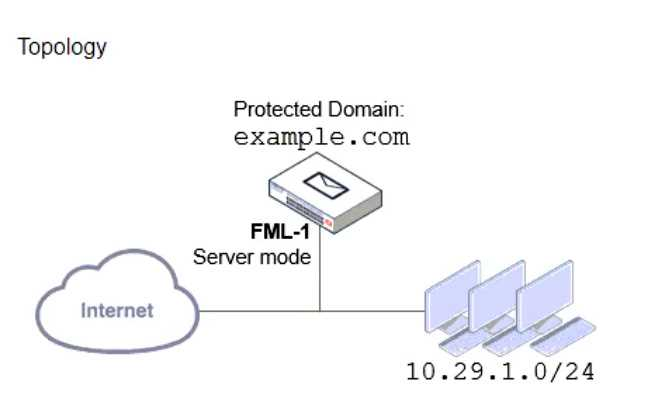
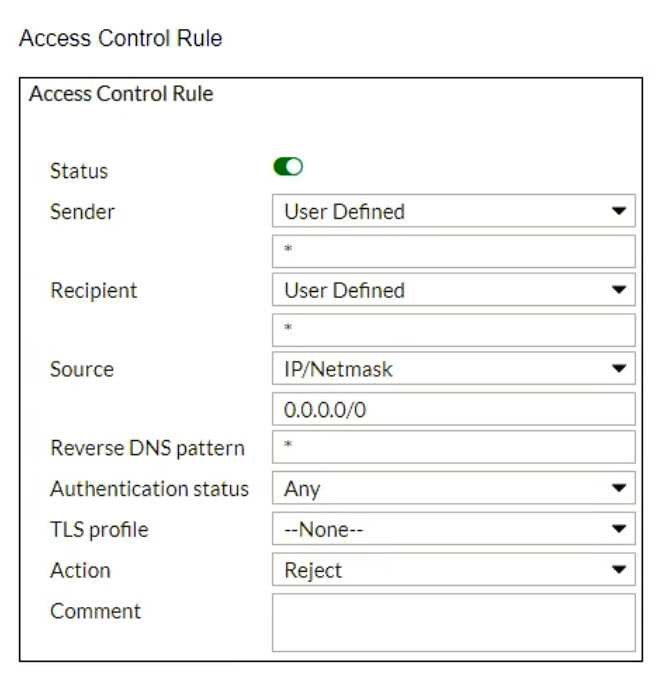
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)
- The Sender IP/netmask should be set to 10.29.1.0/24.
- The Action should be set to Reject
- The Recipient pattern should be set to · @example. com.
- The Authentication status should be set to Authenticated