A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
However, when the penetration tester tried to browse the URL http://172.16.100.10:3000/profile, a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
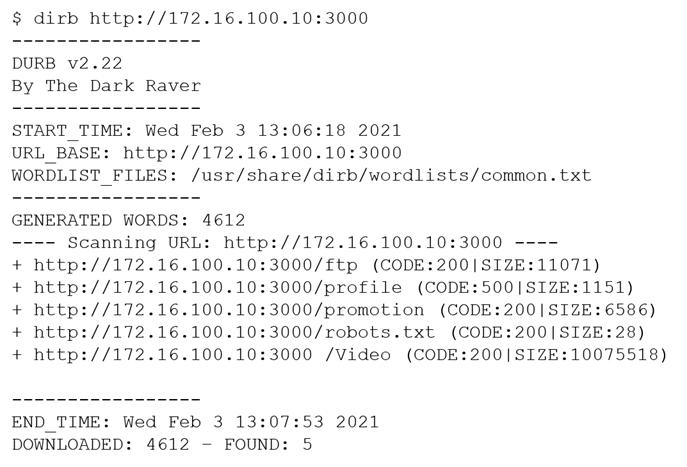
- The HTTP port is not open on the firewall.
- The tester did not run sudo before the command.
- The web server is using HTTPS instead of HTTP.
- This URI returned a server error.